Embedded
Security

Based on many years of experience from several customer projects, we have developed a security offer for you that includes the most important points for your product:
- Know-how and image protection
- Ensuring the availability of your devices and services
- Secure networking and communication of your devices
- Secure remote access for maintenance and service
- Maintaining and expanding the level of security
- Short response times for critical events


Product manager Yves Astein presents the new security packages.
Security measures _ for customized protection
Our software offers are freely accessible and use open-source solutions. For the signing of boot loaders, specific solutions from the controller manufacturer sometimes have to be used.



- security training and individual project advice
- Security features in our standardBSPs and customized solutions
- Secure initialization (Provisioning) at our production site in Mainz (Germany)
- Software Lifecycle Management
We prefer a holistic approach and work according to best practice recommendations as well as the international series of standards for "Industrial communication networks - IT security for networks and systems" (IEC 62443) established in the industry.
In order to make this process as cost-effective as possible for you, we work with a selection of basic methods that can be used to implement a wide variety of security requirements. In practice, just reaching the first security level is a significant improvement in the protection of your product.
| security level (SL) | technical means of the attacker | Resources (time/money) of the attacker | Skills of the attacker | Motivation of the attacker | Confidentiality Damage (after IoTSF) | integrity damage (after IoTSF) | availability damage (after IoTSF) | Significance |
|---|---|---|---|---|---|---|---|---|
| 1 | save | low | save | user error | publication sensitive data | limited | minimal | • Prevention of random user errors • has data loss minimal consequences |
| 2 | general IT knowledge | low | general | low, intentionally aimed | Loss sensitive data | limited | limited | • Scriptkiddy • Data loss has limited Impact on person/organization |
| 3 | highly developed | moderate | system-specific | moderate, intentionally aimed | loss very much sensitive data | limited | high, disastrous | • Prevention of medium attacks (hacker) • has data loss significant influence |
| 4 | highly developed | expanded | system-specific | high, intentionally aimed | loss very much sensitive data | high, disastrous | high, disastrous | • Prevention of major attacks (hackers) (states/organizations) |
Cybercrime is real and the requirements of the legislature are varied and depend on the use of your end product.
Together with you, we determine the legal requirements relevant to your project and decide on the solution.
The following laws apply to the market launch of ITProductsn to note:
- Cyber Security Act - to Products are classified into classes according to the security level
- Product Liability Laws and the state of the art
- Federal Data Protection Act (BDSG)
- IT security law for critical infrastructures (CRITIS)
For a better introduction to the topic, we offer regular training courses on the subject of security. This gives you a comprehensive overview. Subject areas of our training courses include:
- Legal Aspects – Standards and guidelines
– What does the law stipulate?
- Basics (Security Pyramid) – from module to runtime
– What protective measures are there?
- Security by design – Developing secure Productsn
- How is security taken into account in the development process?
- Secure initialization – Safety features in production
– How does your key get onto the module?
- Software Lifecycle Management – Sustainable software maintenance
- How do you provide your product with updates?
Briefly tell us your project requirements and the risks you want to protect yourself against and we will offer you a corresponding in-house workshop or project consultation.
Price from 1800 € / day plus expenses
In our phyBSP Security features already included:
- Secure-Boot for Barebox (NXP-i.MX 6)
- Secure-Boot for u-boot (NXP-i.MX 7, NXP-i.MX 8)
- Signed Linux kernel as a FIT image
- CAAM module for encrypting the file system
The following additional features that are not part of the standardBSPs are can in the form of an individual BSPs are created for your product:
- kernel hardening
- Integration of additional security modules
- Trusted Execution Environment (opt-ee)
- Authentication and secure connection (TLS)

Our service offers:
- Enabling Secure Boot
- Device-specific X509 certificates for authentication for all cloud providers (e.g. Microsoft Azure, AWS, Google IOT), update servers (e.g. MenderIO, FoundriesIO, etc.) or your own server
- Installing a minimal Linux system to simplify final configuration and software installation in your Productsn
- Device registration in the cloud (Microsoft Azure, AWS, Google IOT)
- Activation / deactivation of controller features eg: JTAG
- Encryption of directories or partitions on your device
We are your reliable partner for these tasks, as we can take over the security of your private keys and other secrets during production and software import with our provisioning service in Mainz (Germany).
We ensure maximum security:
- Own production at the location in Mainz
Inspection and auditing are possible and desired - Defined process and roles
- Protected area with restricted access
- Direct contact with the relevant responsible employees (building trust)
- Key sovereignty remains with you
Use of hardware secure modules - No initialization of Productsn for military or secret service use
Risk minimization for you and PHYTEC
Let us create a non-binding offer for you.
Use our software lifecycle management for the sustainable and binding maintenance of the board support packages of your customer-specific hardware. We test your hardware with the latest patches and updates throughout the product lifetime.

You have questions about embedded security
or do you need support for your project?
Our security team will be happy to help you.
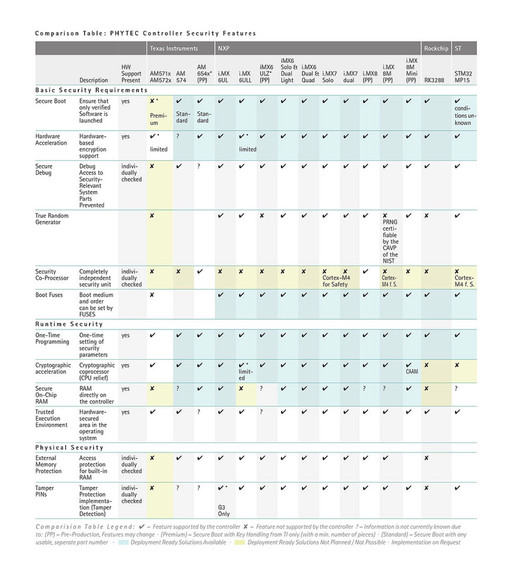
The right controller _ We support you in making the right choice
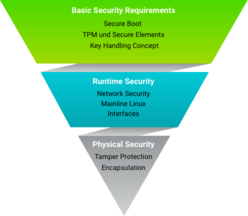
Security Pyramid _ All possible measures to defend against attacks can be roughly divided into three areas.
The following Basic security requirements are the cornerstone for a secure embedded Linux system:
Secure Boot
Using Secure Boot ensures that only trusted, signed software can run on the hardware module. Secure Boot is at the core of the chain of trust. This chain of trust can be used to ensure that only verified software is used right through to the end application.
Trusted Execution Environment (op-tee)
ARM TrustZone is a feature for SoCs and processors in the ARM Cortex-A and Cortex-M processor families. The TrustZone has two separate domains (normal world and secure world). The keys are kept in the secure world, which can be accessed via an API from the normal Linux world. The TrustZone is the basis for the Trusted Execution Environment, of which op-tee is an open source implementation.
eMMC with Replay Protected Memory Block
Secret data can be stored in the RPMB partition, which is protected from unauthorized access.
Device identification
Secure device identification is a fundamental requirement for communication with your devices in networks. To this end, we are working on a process for secure crypto-chip initialization, among other things.
TPM and Secure Elements
Crypto chips and secure elements such as the TPM chip make it possible to store and manage cryptographic keys. The private keys are stored in a tamper-proof manner regardless of the software used.
NXP CAAM
With Secure Boot enabled, the CAAM module from NXP offers similar functionality to a TPM chip, but without the certified physical protection.
Features of the Chain of Trust
- Trusted ROM Bootloader verifies the software image before running it
- Using RSA-4096 key pairs and SHA-256 signatures
- These algorithms meet the requirements of the BSI (Federal Office for Information Security) and the NIST (National Institute of Standards and Technology) until 2030 and beyond
- Basis for setting up a Trusted Execution Environment (TEE) and the ARM TrustZone®
Network Security
When devices communicate with a server or with each other, the connection must be secure. TLS is the most common protocol and application-independent method for implementing an encrypted connection.
- Establish a secure connection regardless of the application or protocol used
- TLS (SSL) is recognized as the best practice and industry standard for encrypted communication
General recommendations
to increase the
application security
- Only run services that you really need on your device
- Close all ports and only open the required ports very selectively
- Always use password-protected logins (including COM and Telnet interfaces)
- Use standard protocols for data transfer
- Use common implementations for encryption (no in-house development)
Mainline Linux
Linux is our first choice as an operating system for industrial series use. One of our clear goals is to offer our customers the advantages of a mainlineBSPs to provide:
- Stable code, fast bug / security fixes as well as the maintenance and further development of mainline drivers by the community
- Mainline is a guarantee for the maintenance of current operating system versions, even after many years
- We often offer both a vendor and a mainlineBSP at the same time. This way you can decide when to get on board with Mainline.
- For phyBOARDBSPs: The latest kernel version with current security patches is included
- For phyBOARDBSPs: The latest Yocto-Minor releases are included
- For phyBOARDBSPs: Annual BSP-Updates with all mainline security patches
- LTS kernel in the BSPs for PHYTEC Products
- Custom testing with continuous integration
interface
All interfaces accessible in the end product are a potential security risk for embedded systems.
- Only use interfaces that are required
- User-dependent access to interfaces
- Use of encrypted connection
In addition to attacks via interfaces or the network connections, direct manipulation of the hardware also represents a security risk. The following methods are available to protect your electronics from physical attacks:
Tamper protection
- Protects sensitive data such as encryption or private keys
- Permanently erases data if the device is tampered with
- A wide variety of realizations are possible
encapsulation (resin casting)
- Physical access to individual components is prevented
- Recognition of the components and parts used is prevented
- Reverse engineering via electrical measurements is not possible

Our embedded experts are there for you!
Secure your personal consultation appointment quickly, easily and free of charge.
30 minutes exclusively for you and your project!
Education + Training _ Use our know-how for yours Productsdevelopment

With the know-how transfer from our experts to your developers, you will reach your goal faster!
Participants in our training courses receive a solid knowledge of professional hardware and software development.

Other interesting topics: